
Magento 2 CSP Whitelisting
This Magento 2 CSP whitelisting module streamlines the creation and management of Content Security Policy (CSP) whitelists. By simplifying the process directly within the Magento 2 admin panel, it eliminates the need for complex code modifications. This user-friendly extension is particularly valuable for Magento 2.4.7 stores with stricter CSP enforcement, allowing for easy whitelist management without compromising security.
- Create and manage CSP whitelists for URLs or hosts directly from the Magento 2 admin panel
- Enable or disable specific CSP directives with individual policy control
- Granular Host Whitelisting
- Dedicated CSP Reports Grid (!New)
- Ability to mass whitelist or delete records from CSP Reports Grid (!New)
- Manage whitelists within a user-friendly interface, streamlining the CSP configuration process..
- No need to modify code with each new module installation or external URL integration, saving development time
- Supports "hash" type CSP Whitelist
- Bypass Magento 2.4.7 restrict mode CSP enforcement easily
- Ensure no critical data points or resources are missing from your store due to CSP
- Compatible with Hyvä theme (!New)


Free Support
up to 60 days


Free Upgrades
up to 1 year


Fully open source
Product description
Magento 2 Content Security Policy (CSP) Whitelisting
Compatible with Magento 2 community and enterprise 2.3.3 - 2.4.x including cloud edition
Content Security Policy (CSP) is a powerful security measure that restricts the resources a web page can load. By implementing a well-defined CSP, you significantly reduce the attack surface of your Magento store, making it more resistant to malicious scripts, injections, and other web-based threats.
This extension grants you complete control over your CSP configuration. The user-friendly interface allows you to effortlessly enable/disable the extension, and configure individual CSP directives. It comes with a dedicated CSP reports grid, that reports all CSP errors on both frontend and backend. These errors can be mass whitelisted from the grid itself.
Problem and the Solution
Running a Magento 2 store is like running a high-end boutique. You want to showcase your products in the best light, attract the right customers, and ensure everything is secure. But unlike a brick-and-mortar store, online threats can lurk in the shadows of your code. That's where Magento 2 Content Security Policy (CSP) comes in – your virtual security guard, keeping the bad guys out and the good guys flowing through.
Imagine CSP as a bouncer with a VIP list. It checks every script, style, and font trying to enter your website against a pre-approved list. Only those on the list (think trusted vendors and your own custom code) get access. This significantly reduces the risk of malicious code injection, a tactic hackers use to steal data or take control of your site.
Here's the catch: overly strict CSP rules can be like an overzealous bouncer, turning away legitimate customers (read: essential functionalities). You might find your fancy product sliders malfunctioning or social media buttons disappearing. This can lead to frustrated shoppers and lost sales – not exactly the outcome you're looking for.
So, how do you strike the balance between security and functionality? Enter user-friendly Magento 2 CSP whitelisting module. This acts like velvet ropes at your virtual door. You can easily create and manage whitelists for trusted URLs and domains directly from your Magento 2 admin panel. No more wrestling with complex code!
Identifying and Fixing Magento CSP Errors
Through CSP Reports Grid
- Make sure extension is configured properly(refer userguide), go to Admin>System>Scommerce CSP Records>CSP Report Only Grid
- Select all the CSP violations that you want to whitelist and then from the Actions dropdown click Whitelist, it will whitelist all the selected records.

Manually
- Open your site in Google Chrome Browser
- Check console logs
- Each CSP error will have Content Security Policy directive (for example img-src, connect-src, script-src) etc. along with host name.
- For example Refused to load the image 'https://region1.google-analytics.com/g/collect...' because it violates the following Content Security Policy directive: "content-src...". In this example content-src is the policy id and .region1.google-analytics.com is the host which can be added in the configuration to fix this error

- Once identified simply add in all the hosts visible in the above image, in extension configuration under the directive "content-src" . After which this error will no longer be displayed in the console and the host shouldn't be blocked anymore.
CSP Directives: Explained
Here we will explain each of CSP directives in detail so that you are able to better identify the error in your browser console and make the appropriate entries in the module to fix them. Here's a breakdown of common CSP directives and their explanations:
-
default-src
- Purpose: Sets the default policy for loading content such as JavaScript, images, CSS, fonts, AJAX requests, and frames. If other directives are not specified, this policy will be applied.
- Example:
default-src 'self' - Explanation: Allows content to be loaded only from the same origin as the page.
-
script-src
- Purpose: Controls what JavaScript can be executed on the page.
- Example:
script-src 'self' https://apis.google.com - Explanation: Allows scripts to be loaded from the same origin and Google's API services.
-
style-src
- Purpose: Specifies the sources for stylesheets.
- Example:
style-src 'self' 'unsafe-inline' https://fonts.googleapis.com - Explanation: Allows styles from the same origin, inline styles (which can be risky), and Google Fonts.
-
img-src
- Purpose: Defines from where images can be loaded.
- Example:
img-src 'self' https://images.example.com - Explanation: Allows images to be loaded from the same origin and a specific image CDN.
-
connect-src
- Purpose: Limits the origins that can be connected to via scripts (like AJAX calls).
- Example:
connect-src 'self' https://api.example.com - Explanation: Only allows connections to the same origin and a specific API endpoint.
-
font-src
- Purpose: Controls the sources for web fonts.
- Example:
font-src 'self' https://fonts.gstatic.com - Explanation: Allows fonts to be loaded from the same origin and Google Fonts CDN.
-
object-src
- Purpose: Specifies valid sources for the
<object>,<embed>, and<applet>tags. - Example:
object-src 'none' - Explanation: Disallows all usage of these tags, enhancing security.
- Purpose: Specifies valid sources for the
-
media-src
- Purpose: Controls the origins from which media files (like audio and video) can be loaded.
- Example:
media-src 'self' https://media.example.com - Explanation: Allows media to be loaded from the same origin and a specific media CDN.
-
frame-src
- Purpose: Specifies valid sources for nested browsing contexts using
<frame>and<iframe>. - Example:
frame-src 'self' https://trustedpartner.com - Explanation: Allows iframes from the same origin and a trusted partner site.
- Purpose: Specifies valid sources for nested browsing contexts using
-
child-src
- Purpose: Specifies valid sources for web workers and nested browsing contexts (like iframes).
- Example:
child-src 'self' https://example.com - Explanation: Allows web workers and iframes from the same origin and a specific site.
-
worker-src
- Purpose: Controls the sources for Worker, SharedWorker, or ServiceWorker scripts.
- Example:
worker-src 'self' - Explanation: Allows worker scripts to be loaded from the same origin.
-
form-action
- Purpose: Specifies which URLs can be used as the target of form submissions.
- Example:
form-action 'self' https://forms.example.com - Explanation: Allows form submissions to the same origin and a specific forms endpoint.
-
frame-ancestors
- Purpose: Specifies valid parents that may embed a page using
<frame>,<iframe>,<object>,<embed>, or<applet>. - Example:
frame-ancestors 'self' https://trustedpartner.com - Explanation: Allows the page to be framed only by the same origin and a trusted partner.
- Purpose: Specifies valid parents that may embed a page using
-
base-uri
- Purpose: Restricts the URLs which can be used in a document’s
<base>element. - Example:
base-uri 'self' - Explanation: Allows the base URL to be set only to the same origin.
- Purpose: Restricts the URLs which can be used in a document’s
-
report-uri
- Purpose: Specifies the URL where the browser sends reports about policy violations.
- Example:
report-uri https://report.example.com/csp-violations - Explanation: Violations of the CSP are reported to the specified URL.
-
report-to
- Purpose: Defines a reporting group which can be used to specify endpoints for reporting.
- Example:
report-to csp-endpoint - Explanation: Utilizes the
Reporting-Endpointsdefined in theReport-Toheader for CSP violations.
The main highlights of the module are-:.
- Effortless Whitelisting: Easily add whitelisted resources for various CSP policies (script-src, style-src, etc.) through a user-friendly interface. No more manual configuration hassles!
- Enhanced Security: Maintain a secure environment by whitelisting only trusted resources while mitigating Cross-Site Scripting (XSS) and other attacks.
- Streamlined Workflow: Save valuable development time with straightforward configuration.
- Improved User Experience: Eliminate broken functionality and ensure a seamless user experience for your customers.
- Granular Control: Define whitelisted resources by domain, subdomain, or specific URL path for maximum security.
- Multi-Store Support: Manage whitelists for multiple Magento 2 stores from a single location.
- Ensure you are ready for Magento 2.4.7 restrict mode CSP enforcement.
- Supports "hash" type CSP Whitelist for style and Script Src CSP errors(NEW!)
- Dedicated CSP Reports Grid to analyze and manage all CSP errors(NEW!)
- The CSP Grid includes mass whitelist or delete feauture allowing you to whitelist multiple CSP violations with a click of a button(NEW!)
- The extension is fully compatible with Hyvä theme(NEW!)
- Easy to install and manage
- Flexible and user-friendly interface.
- Easy configuration
- It can be easily disabled from admin interface.
We offer 60 days of free support and 12 months of free upgrade for any standard Magento site when you buy this extension. You can also get our installation service for a small fee. If you want more benefits, you can purchase our 12 months of free premium support and free lifetime upgrade package. Please contact us if you need any assistance or customization for this extension. We will reply to you within 48 hours. We may also offer you a special deal or a free solution if we like your idea.
** Please refer to our FAQ or T&C section for running our extensions on multiple domains or sub-domains
FAQ
Frequently Asked Questions

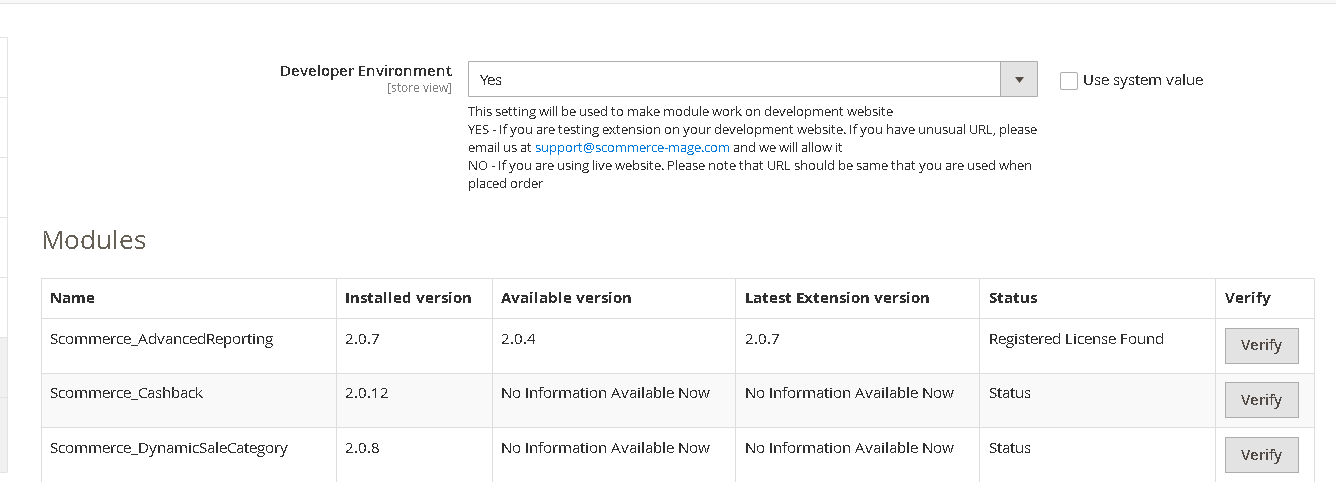
Once added go to Stores>Configuration>Scommerce Configuration> Core and set "Development Environment" to "Yes" then click on verify. Once verified the license will start working on your staging site.
https://www.scommerce-mage.com/magento-extension-installation-service.html
Once you received the latest version of our extension then we would highly recommend to delete all the files and folder of our extension from your website first before uploading the latest version because we might have removed existing files and keeping existing files could cause problems on your website.
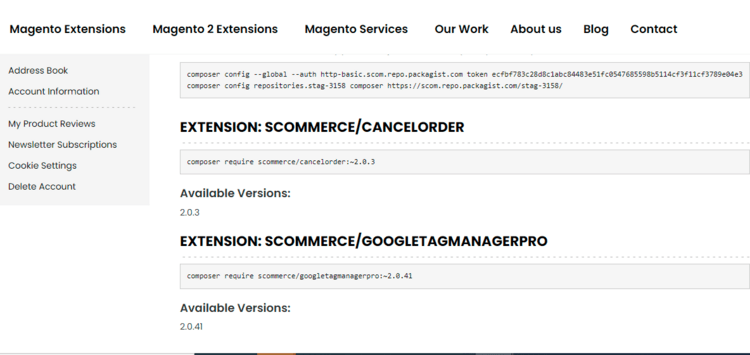
 Step 2: Next, run the config commands shown on the top of the page then click on the extension that you want to install. A composer require command will be revealed in the dropdown menu. Run the command then clear caches to complete the installation.
Step 2: Next, run the config commands shown on the top of the page then click on the extension that you want to install. A composer require command will be revealed in the dropdown menu. Run the command then clear caches to complete the installation.
Change Log
Reviews 1
- Magento 2
 Magento 2 Advanced Admin Login SecurityEnhance the security of your Magento 2 admin panel with our comprehensive Magento 2 Advanced Admin L...£84.99
Magento 2 Advanced Admin Login SecurityEnhance the security of your Magento 2 admin panel with our comprehensive Magento 2 Advanced Admin L...£84.99 - Magento 2
 Magento 2 Security ChecklistIn an era where digital threats loom large, the "Magento 2 Security Checklist" by Scommerce Mage sta...£84.99
Magento 2 Security ChecklistIn an era where digital threats loom large, the "Magento 2 Security Checklist" by Scommerce Mage sta...£84.99 - Magento 2
 Magento 2 Security SuiteElevate the security of your Magento 2 store with our comprehensive Magento 2 Security Suite. Design...£199.99
Magento 2 Security SuiteElevate the security of your Magento 2 store with our comprehensive Magento 2 Security Suite. Design...£199.99 - Magento 2Breeze
 Magento 2 Admin Action LogMagento 2 Admin Activity Logger extension is developed to improve the security of your store and pro...£124.99
Magento 2 Admin Action LogMagento 2 Admin Activity Logger extension is developed to improve the security of your store and pro...£124.99





